This repository was archived by the owner on Dec 5, 2025. It is now read-only.
-
-
Notifications
You must be signed in to change notification settings - Fork 365
This repository was archived by the owner on Dec 5, 2025. It is now read-only.
New deployment, Narnia of new Fun #1894
Copy link
Copy link
Closed
Labels
Description
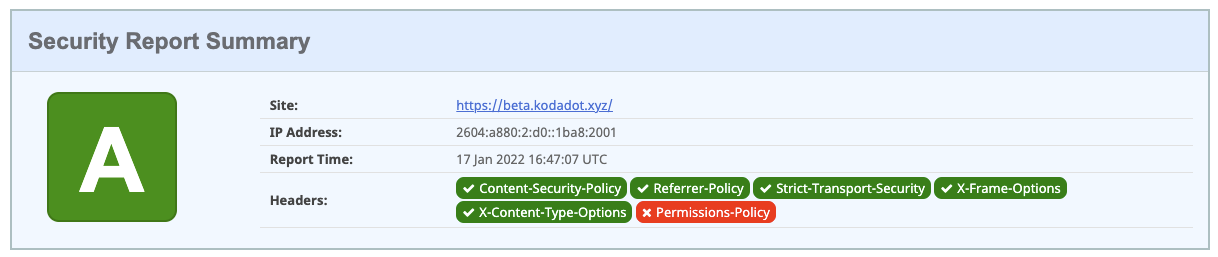
https://securityheaders.com/?q=https%3A%2F%2Fkodadot.xyz&followRedirects=on
We've had A back at Netlify, time to fix this stuff again on Cloudflare
From Netlify.toml -- https://github.com/kodadot/nft-gallery/blob/main/netlify.toml
[headers.values]
X-Frame-Options = "DENY"
X-XSS-Protection = "1; mode=block"
# Referrer Policy is a new header that allows a site to control how much information the browser includes with navigations away from a document and should be set by all sites.
Referrer-Policy = "strict-origin-when-cross-origin"
# Don't load any resource type not explicitly enabled
# Disable plugins like Flash or Silverlight
# Load images, scripts, stylesheets and fonts from self
## Content-Security-Policy = "upgrade-insecure-requests" <- this did not work tho
# Prevent browsers from incorrectly detecting non-scripts as scripts
X-Content-Type-Options = "nosniff"
# Block site from being framed with X-Frame-Options and CSP
Content-Security-Policy = "frame-ancestors 'self';"
# Basic one if one above won't work
# Content-Security-Policy = "default-src 'self';"
# For future testing, refer to https://github.com/kodadot/nft-gallery/issues/540
# Permissions-Policy = "interest-cohort=()"Seems on https://beta.kodadot.xyz it's working well