-
Notifications
You must be signed in to change notification settings - Fork 4.4k
Closed
Description
Describe the bug
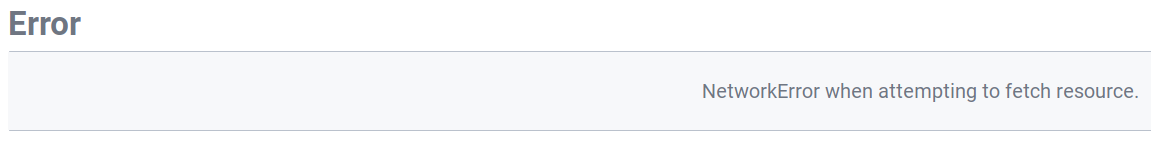
We have Vault running with UI enabled. We found one secret that is only readable via CLI. If we try to read it via UI we get the following error:
Details
If found that a 403 is given by sys/internal/ui/resultant-acl. When given access to this path via policy this specific 403 disappears and the audit log show valid response data for sys/internal/ui/resultant-acl. But the secret is still not readable and gives the same UI error. I've tried deleting and replacing the secret to no avail.
Environment:
- Vault Server Version (retrieve with
vault status): 1.3.4 - Vault CLI Version (retrieve with
vault version): 1.1.3 - Server Operating System/Architecture: CentOS7 x86_64
Vault server configuration file(s):
Vault config:
{
"listener": {
"tcp": {
"address": "0.0.0.0:8200",
"tls_cert_file": "/etc/ssl/aperto/cert.crt",
"tls_key_file": "/var/lib/vault/tls/cert.key",
"tls_min_version": "tls12",
"tls_cipher_suites": "TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"tls_prefer_server_cipher_suites": "true",
"tls_disable_client_certs": "true"
}
},
"storage": {
"file": {
"path": "/var/lib/vault"
}
},
"default_lease_ttl": "24h",
"max_lease_ttl": "817600h",
"ui": "true"
}Combined policy
# Allow access to the random path
path "sys/tools/random" {
capabilities = [ "update" ]
}
# Allow access to the hashing path
path "sys/tools/hash" {
capabilities = [ "update" ]
}
# Disallow usage of cubbyhole to avoid confusion on removed secrects
path "cubbyhole/*" {
capabilities = [ "deny" ]
}
path "TEAM/*" {
capabilities = [ "create", "list", "update", "read", "delete" ]
}
# one time password engine for 2FA
path "totp/*" {
capabilities = [ "create", "list", "update", "read", "delete" ]
}
# allow creation of child tokens
# this is currently used for terraform vault access
path "auth/token/create" {
capabilities = [ "update", "create" ]
}
# allow managing ldap configuration
path "auth/ldap/config" {
capabilities = [ "read", "update" ]
}Additional context
Currently the problem only persists for this one entry under TEAM/server/SERVER_FQDN/piwik/admin
Metadata
Metadata
Assignees
Labels
No labels